Over the past 17 years, Bitcoin has evolved in the public eye. Every transaction, every protocol upgrade, and every increase in hashrate has been recorded on an open network and debated in public forums. At the same time, another field has been advancing largely out of view: quantum computing.
Unlike Bitcoin, progress in quantum does not unfold on a 24/7 public ledger. These advances often arrive in the public eye as sudden announcements, sparking fresh debates about Bitcoin's cryptographic foundations. But understanding what quantum actually affects helps separate signal from noise.
Bitcoin’s security rests on two cryptographic foundations that predate the network and are widely used across modern computing systems. Elliptic curve cryptography (ECC) underpins Bitcoin’s digital signature scheme, ECDSA, which proves ownership and authorizes spending, while SHA-256 is the hash function that secures mining and protects the integrity of the blockchain. Both remain strong under today's computing assumptions. That strength is reinforced by an unprecedented level of classical computing power with the network's hashrate recently crossing the one-zettahash threshold. Fittingly, that’s a 1 followed by 21 zeros.
While classical machines process binary bits one by one, quantum systems use properties like superposition, entanglement, and interference to process information all at once. This leap from linear processing to parallel problem-solving means quantum computers can handle calculations previously considered impossible for classical machines.
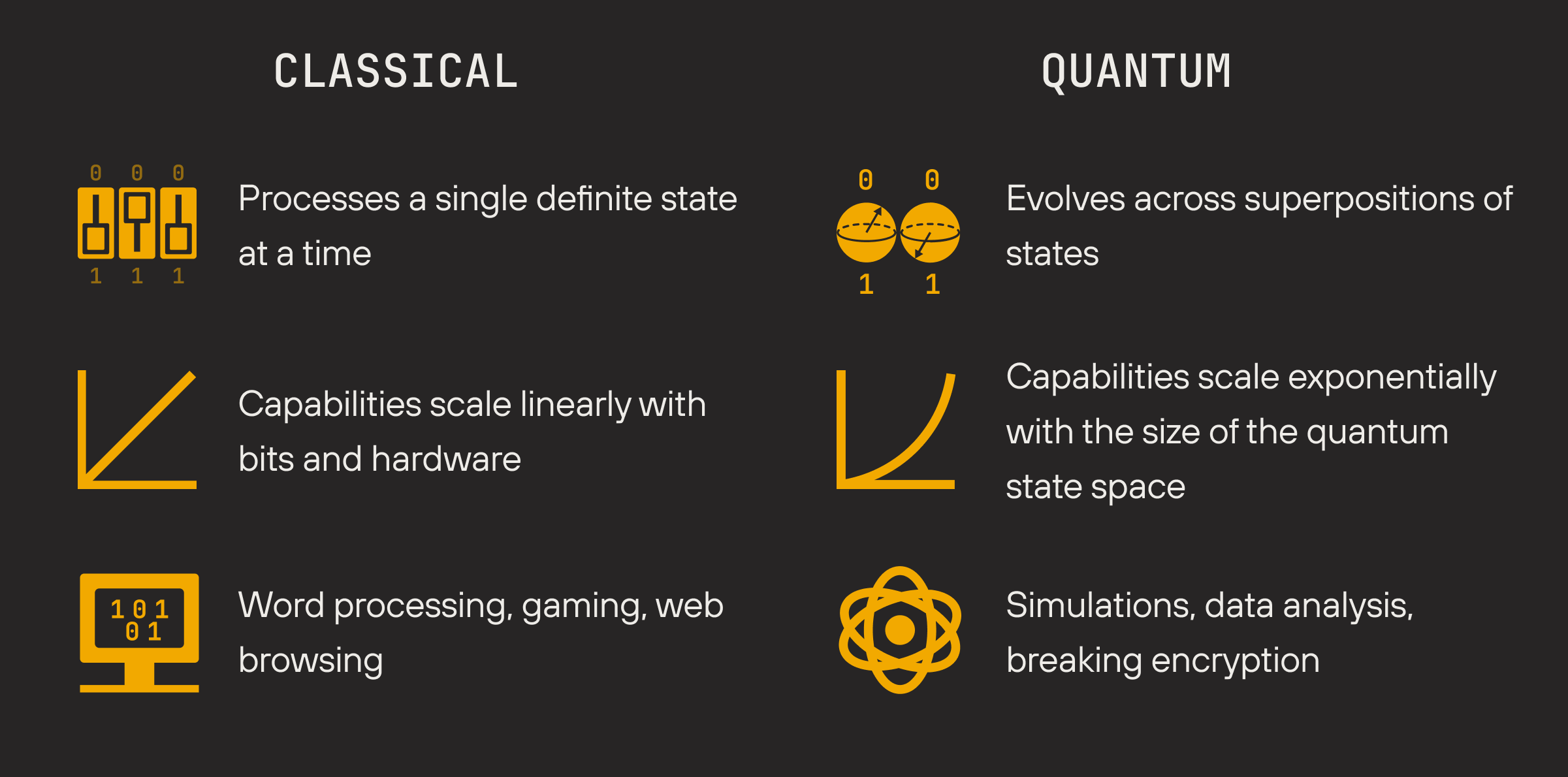
This is why they matter for cryptography: algorithms like Shor's could eventually weaken the math behind digital signatures, potentially allowing private keys to be derived from exposed public keys, enabling unauthorized spending of funds. Under most credible quantum scenarios, this risk concentrates on signature schemes like ECDSA rather than the hash functions that secure the structure of the blockchain itself. The practical question, then, is important: could a sufficiently powerful quantum computer be used to spend coins without the owner’s authorization?
No such computer exists today, and meaningful advances would be visible well before they pose real danger. But because Bitcoin evolves deliberately and upgrades take time, often years, preparation works best when it begins early.
Why Some Bitcoin is More Vulnerable Than Others
This is the most underreported part of the quantum story: not all bitcoin face equal risk. Exposure depends entirely on what's been published on-chain.
The critical vulnerability requires a visible public key. If an attacker can see your public key, a future quantum computer could theoretically derive your private key from it. If your public key has never been revealed, there's nothing to attack.
Public key visibility establishes levels of exposure.
- Highest risk: Coins whose public keys are permanently on-chain. This includes coins unmoved for many years from Bitcoin’s earliest epoch and coins held at reused addresses after a spend has revealed the public key. In both cases, the key is a known target with effectively unlimited time for attack in any future quantum scenario.
- Lowest risk: Modern hashed formats. Most commonly used address types today keep public keys hashed on-chain. The actual key is revealed only at the moment of spending, then the address is effectively retired. Any hypothetical attacker would need to act within the narrow window between broadcast and confirmation. This window is measured in minutes, not years.
Some coins are more exposed than others based on how they are held and how much information has been revealed on-chain. Risk scales with exposure, and users largely control how exposed their keys are.
The Response: What's Already Being Built
Bitcoin's deliberate pace of change turns out to be well-suited to long-horizon threats. There's time to study, test, and coordinate across multiple layers of preparation. But time alone doesn't solve problems. It only creates the window for builders to solve them. That work is underway, but these researchers and developers could always use reinforcements.

Protocol-level solutions: Developers are designing quantum-resistant output types through proposals like BIP 360, which fixes the inherent vulnerability in Taproot outputs and allows an upgrade path to post-quantum signature schemes. This work proceeds through Bitcoin's open process, with the expectation that solutions will be tested extensively before any mainnet consideration.
Damage limitation: Other proposals focus on slowing potential attacks rather than preventing them outright. The Hourglass proposal, for instance, explores rate-limiting the movement of some quantum-exposed coins. If an attack ever materialized, this would reduce market disruption and buy time for coordinated response.
Migration strategies: Proposals like the "Post Quantum Migration and Legacy Signature Sunset" outline phased soft forks with firm deadlines — creating incentives to migrate before vulnerable addresses are frozen. The approach is deliberately forceful, designed to overcome upgrade inertia before a quantum threat materializes. This migration, however, operates under the assumption that quantum resistant address types already exist, through proposals like BIP 360.
Efficiency and size: Proposals like Jonas Nick’s hash-based optimizations reduce the data footprint of post-quantum signatures to keep the blockchain lean. This technical groundwork pairs with "emergency hatches" like Tadge Dryja’s Lifeboat, which allows users to secure assets without requiring a soft fork. Together, these tools provide the lightweight infrastructure and immediate protections needed to defend the network long before a full migration.
Private Mempools: To avoid exposing public keys, private mempools such as MARA Slipstream may become essential to more securely facilitate the quantum migration. This can be integrated directly into wallets and transaction submission encrypted using post-quantum cryptography.
Testing infrastructure: Major upgrades to Bitcoin require broad agreement and years of vetting. Sidechains provide a way to test quantum-resistant designs under real conditions without risking the main network. Programs like Anduro use this approach, experimenting with new signature schemes and migration mechanics in controlled environments, generating evidence about what works before anything is proposed for Bitcoin itself.
The goal across all these efforts is optionality. By developing solutions early, Bitcoin preserves the ability to respond thoughtfully if and when the threat materializes, without committing prematurely to changes that might prove unnecessary.
What You Can Do Now
So what are some practical steps anyone could take today to reduce their exposure that don't require waiting for protocol changes?
Avoid address reuse. Once you've spent from an address, don't receive new funds there. Most modern wallets handle this automatically, generating a fresh address for each transaction.
Use wallets that follow current best practices. Modern address formats typically keep public keys hashed on-chain until the moment of spending, reducing long-term exposure without requiring users to understand the underlying cryptography.
Be mindful of address types. Native SegWit formats such as P2WPKH and P2WSH combine lower fees with hashed public key commitments, making them a conservative choice for long-term storage. Some newer wallet types like Taproot prioritize efficiency or functionality over minimizing key exposure, which may be less desirable for holding large balances over long periods.
Understand your own situation. If you hold coins in old addresses, or have historically reused addresses, your exposure is higher. This doesn't mean panic, but it might mean prioritizing a move to fresh addresses when convenient.
Don't overthink it. For most users following modern practices, quantum risk is already minimized by default. The largest exposures belong to dormant early-era coins and specific edge cases, not typical active wallets.
The Bottom Line
Because the timing and scale of any quantum threat remain uncertain, the prudent approach is neither alarm nor complacency, but preparation. Taking reasonable, incremental steps today reduces exposure without forcing premature changes.
Preparation over panic gives Bitcoin the best path to a smooth transition to post-quantum security, if and when it becomes necessary.
Most users already benefit from address formats that limit exposure. And the groundwork for broader solutions is underway. The ecosystem is actively building broader solutions, testing them carefully, and coordinating deliberately. But none of this runs on autopilot. The work needs researchers, developers, and scrutiny.
Bitcoin has time to get this right, and its ability to do so improves with every step taken today.
Follow @andurobtc on X for real-world experimentation on post-quantum Bitcoin infrastructure.






.avif)



